This post features a script derived from Jan Markowski's published in 2600: Volume 37, Issue 1 (Spring 2020)
Trying to keep track of passwords is no easy chore. If you opt to use the same password for all accounts, you will eventually rue the day! Several months ago, I had too many ‘did you just login from…’ notifications, so I undertook the grand task of creating unique passwords for ALL my online accounts.
This sucked…
I have a list of roughly 375 logins; took me nearly a week (several hours a day, each day) to finish. Some websites didn’t even have a change password option, so it required me to use “forgot password” functions. This amount of data retention is unmanageable for anyone, so it coincided with my transition to 1Password. Other password managers (Google, LastPass, DashLane,etc) exist, but I got a great deal on 1Password and I wanted something more portable than Google with Yubikey potential down the road.
That part doesn’t matter, but what does is that several managers provide a “Compromised Password” check feature. 1Password’s “Watch Tower” function is able to determine any vulnerable and compromised passwords in your list. You may really wonder what resources these companies hoard, but the truth is much simpler. They use a third-party: haveibeenpwned.com database.
What is HaveIBeenPwned (HIBP)?
Collected over the years, founder Troy Hunt was keen on providing a free resource in the after math of public data breaches. Companies at the time (and still today) failed to get word down to consumers/users/employees/etc in a timely fashion following personal information leaks. The InfoSec community still sees a lack of reporting when businesses are not legally required to or when personal information could not be determined to have left their systems or control. Troy’s system is the best of the gray world we live in, but is it a good idea?
I never felt fully comfortable with HaveIBeenPwned.com. I certainly appreciate the effort, but sharing account info or passwords makes me cringe. Their main page can be used for username/email account enumeration to start with. After a compromised account is flagged, nefarious fellas can go track down the legacy data breach information and get to work on abusing accounts. This could still be done without HIBP, but the site provides a quick cross-check against which data breach was the source. And this is all traversing the internet. In order to check this database, you have to share your login/email; all private or sensitive info to you. Is that logged somewhere along the way and also open to abuse?
Is there a better way to check your passwords? Sure!
PwnedPasswords API
This feature was developed to allay these concerns.
The method works like this:
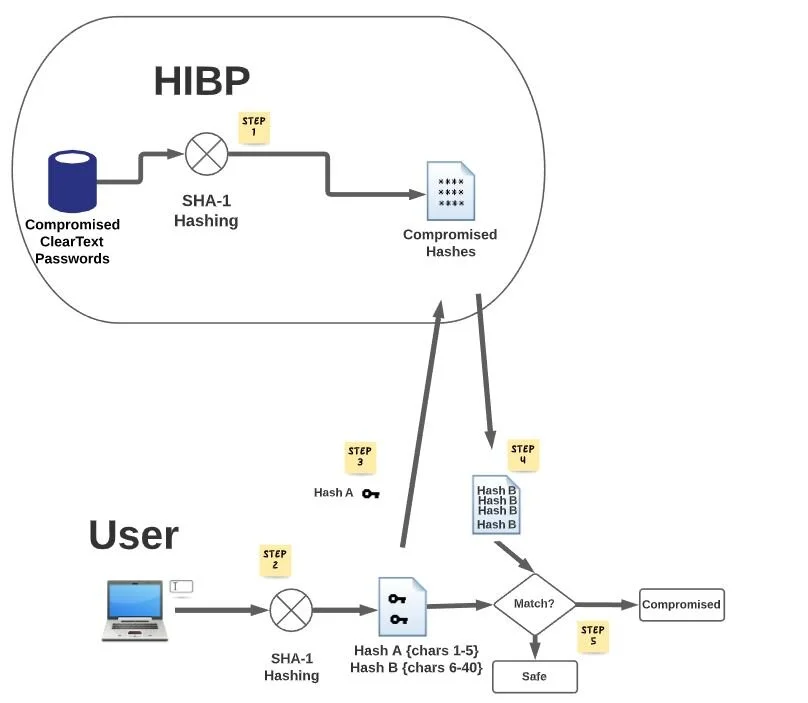
Haveibeenpwned creates SHA1 hashes of all compromised passwords found in dark web disclosures/sales.
You locally generate a SHA1 hash of your favorite password (totaling 40 characters).
You submit the first 5 characters of the hash to HIBP.
HIBP sends a list of all hashes in the database which match the first 5 characters.
** NOTE ** No password has been shared…only the 5 chars of a hash (irreversible) were transmitted
Look at the list containing characters 6-40 and match your hash personally to determine if you were exposed.
Why use the API?
With the normal HIBP website, you would submit your account or email address. If you change passwords frequently, you will only know which account (not password) was compromised. By specifically comparing password hashes, you get more fidelity of which password and possibly when you were compromised.
If you reuse passwords, knowing you are compromised doesnt matter as much as knowung which password you need to stop using.
Is there an easy way to check my passwords?
Yes! I grabbed a bash shell script featured in the Spring 2020 issue of 2600 magazine and tested it out successfully. Great, but what about those who don’t use Linux? I’ve taken my python skills out of the drawer and made an equivalent script available on GitHub at: https://github.com/ParityInfosec/safepwncheck.
This Python3 script is OS agnostic and takes either a single password or a file of passwords as an argument. Locally the script performs the hash function for each password and then checks the whole hash against the returns from HIBP. This keeps everything in your hands and more importantly, on your box!
Beware: Handling password files can be dangerous. Use all precautions in storing this data to prevent compromise of known passwords. This should include limiting file permissions and encrypting data while at rest as needed. Further, any command line logs (i.e. powershell/bash history) should be wiped or redirected to null if passwords were entered in clear text via a shell interface.